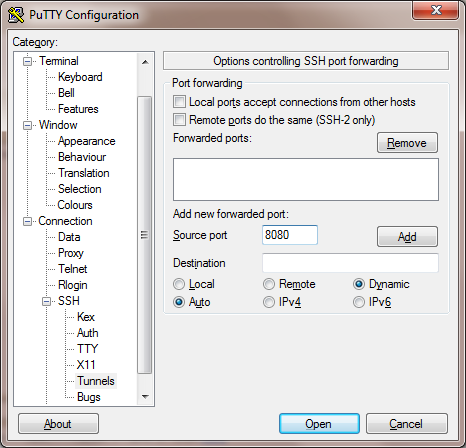
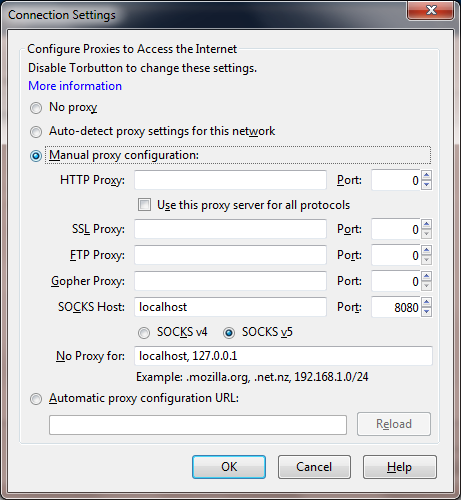
Well this is going to be a two part hack. I configured a cisco switch for 3 diffrent VlAN's I'll be using 2 of the VLAN's please look at the config for any questions this is on a Catalyst 3500 XL switch.
Continue with configuration dialog? [yes/no]:
% Please answer 'yes' or 'no'.
Continue with configuration dialog? [yes/no]:
% Please answer 'yes' or 'no'.
Continue with configuration dialog? [yes/no]: no
Press RETURN to get started.
Switch>en
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int
% Incomplete command.
Switch(config)#
Switch(config)#interface ?
FastEthernet FastEthernet IEEE 802.3
GigabitEthernet GigabitEthernet IEEE 802.3z
Multilink Multilink-group interface
Port-channel Ethernet Channel of interfaces
VLAN Switch VLAN Virtual Interface
Virtual-TokenRing Virtual TokenRing
Switch(config)#interface
% Incomplete command.
Switch(config)#interface Fast
Switch(config)#interface FastEthernet0/1
Switch(config-if)#?
Interface configuration commands:
arp Set arp type (arpa, probe, snap) or timeout
bandwidth Set bandwidth informational parameter
carrier-delay Specify delay for interface transitions
cdp CDP interface subcommands
custom-queue-list Assign a custom queue list to an interface
default Set a command to its defaults
delay Specify interface throughput delay
description Interface specific description
duplex Configure duplex operation.
exit Exit from interface configuration mode
fair-queue Enable Fai
help Description of the interactive help system
hold-queue Set hold queue depth
keepalive Enable keepalive
load-interval Specify interval for load calculation for an
interface
logging Configure logging for interface
loopback Configure internal loopback on an interface
mac-address Manually set interface MAC address
max-reserved-bandwidth Maximum Reservable Bandwidth on an
media-type Interface media type
mtu Set the interface Maximum Transmission Unit
(MTU)
mvr MVR per port configuration
negotiation Select Autonegotiation mode
no Negate a command or set its defaults
port Perform switch port configuration
power power configuration
priority-group Assign a priority group to an interface
random-detect Enable Weighted Random Ea
Interface
rmon Configure Remote Monitoring on an interface
service-policy Configure QoS Service Policy
shutdown Shutdown the selected interface
snmp Modify SNMP interface parameters
spanning-tree Spanning Tree Subsystem
speed Configure speed operation.
switchport Set switching mode characteristics
timeout Define timeout values for this interface
transmit-interface Assign a transmit interface to a
receive-only
interface
tx-queue-limit Configure card level transmit queue limit
udld Configure UDLD enabled or disabled and
ignore global
UDLD setting
Switch(config-if)#^Z
Switch#
00:13:29: %SYS-5-CONFIG_I: Configured from console by consoleshow vtp
status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 254
Number of existing VLANs : 5
VTP Operating Mode : Server
VTP Domain Name :
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0xBF 0x86 0x94 0x45 0xFC 0xDF 0xB5
0x70
Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- ---------
--------------------------
1 default active Fa0/1, Fa0/2, Fa0/3,
Fa0/4,
Fa0/5, Fa0/6, Fa0/7,
Fa0/8,
Fa0/9, Fa0/10, Fa0/11,
Fa0/12,
Fa0/13, Fa0/14,
Fa0/15, Fa0/16,
Fa0/17, Fa0/18,
Fa0/19, Fa0/20,
Fa0/21, Fa0/22,
Fa0/23, Fa0/24,
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode
Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- --------
------ ------
1 enet 100001 1500 - - - - - 1002
1003
1002 fddi 101002 1500 - - - - - 1
1003
1003 tr 101003 1500 1005 0 - - srb 1
1002
1004 fdnet 101004 1500 - - 1 ibm - 0
0
1005 trnet 101005 1500 - - 1 ibm - 0
0
Switch#vlan database
Switch(vlan)#vtp server
Device mode already VTP SERVER.
Switch(vlan)#vlan 2 name test
VLAN 2 added:
Name: test
Switch(vlan)#exit
APPLY completed.
Exiting....
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --
1 default active Fa0/1, Fa0/2, Fa0/3,
Fa0/4,
Fa0/5, Fa0/6, Fa0/7,
Fa0/8,
Fa0/9, Fa0/10, Fa0/11,
Fa0/12,
Fa0/13, Fa0/14,
Fa0/15, Fa0/16,
Fa0/17, Fa0/18,
Fa0/19, Fa0/20,
Fa0/21, Fa0/22,
Fa0/23, Fa0/24,
2 test active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode
Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- --------
------ ------
1 enet 100001 1500 - - - - - 1002
1003
2 enet 100002 1500 - - - -
1002 fddi 101002 1500 - - - - - 1
1003
1003 tr 101003 1500 1005 0 - - srb 1
1002
1004 fdnet 101004 1500 - - 1 ibm - 0
0
1005 trnet 101005 1500 - - 1 ibm - 0
0
Switch#vlan database
Switch(vlan)#vtp server
Device mode already VTP SERVER.
Switch(vlan)#vlan 3 name test2
VLAN 3 added:
Name: test2
Switch(vlan)#exit
APPLY completed.
Exiting....
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int vlan2
Switch(config-subif)#management
Switch(config-subif)#
Switch#
00:19:43: %SYS-5-CONFIG_I: Configured from console by consoleconfig t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int fa
Switch(config)#int fastEthernet 0/5
Switch(config-if)#switchport access vlan2
^
% Invalid input detected at '^' marker.
Switch(config-if)#switchport access vlan 2
Switch(confi
Switch(config)#inter
Switch(config)#interface fast
Switch(config)#interface fastEthernet 0/6
Switch(config-if)#switchport access vlan 2
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/7
Switch(config-if)#switchport access vlan 2
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/10
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/11
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#interface fastEther
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#end
Switch#write
00:23:15: %SYS-5-CONFIG_I: Configured from console by console memorey
^
% Invalid input detected at '^' marker.
Switch#write memory
Building configuration...
[OK]
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4,
Fa0/8, Fa0/9, Fa0/13, Fa0/14,
Fa0/15, Fa0/16, Fa0/17, Fa0/18,
Fa0/19, Fa0/20, Fa0/21, Fa0/22,
Fa0/23, Fa0/24, Gi0/1, Gi0/2
2 test active Fa0/5, Fa0/6, Fa0/7
3 test2 active Fa0/10, Fa0/11, Fa0/12
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 1002 1003
2 enet 100002 1500 - - - - - 0 0
3 enet 100003 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 1 1003
1003 tr 101003 1500 1005 0 - - srb 1 1002
1004 fdnet 101004 1500 - - 1 ibm - 0 0
1005 trnet 101005 1500 - - 1 ibm - 0 0
Switch#